The topic of cybersecurity is gaining increasing attention from businesses, the media, and individuals, but unfortunately for the wrong reasons, as the main cause for this increase is the steep growth of the number of cyberattacks and their severity. Nevertheless, it is always extremely beneficial to raise awareness about this type of issue, regardless of the cause, since the best defense against these cyberattacks is you, the user, and the knowledge that you behold. Therefore, this article is an excellent starting point for people who want to be introduced to the cybersecurity world, understand and protect themselves from the most common threats/attacks they face or have faced on a daily basis, and gain insight into the future of this field.
The main goal is that after reading the article, you will feel keen to investigate more about this subject and become more aware of the threats that surround you.
What is Cybersecurity?
Certainly, you have already heard stories about the importance of cybersecurity or news stories about attacks on a company carried out by a particular cybercriminal. However, let’s take a step back and start with a simple definition. Cybersecurity is the practice of protecting data from malicious attacks by hardening computers, servers, mobile devices, electronic systems, and networks. It is also referred to as information technology security or electronic information security.
Why is it so important?
In this day and age, when data/information is one of the most valuable commodities, one can even argue that it is the most valuable one, the temptation to obtain it by any means possible in order to profit from it is growing exponentially. Another factor contributing to this increase is the easy access to tools and information that allow an individual to easily carry out cyberattacks that can completely undermine a company’s reputation. Therefore, now more than ever, cybersecurity practices must be applied to all areas and assets of an organization as the attack surface, i.e., the number of users, devices and programs, continues to grow.
Most common attacks, and how to prevent them.
The attacks presented in this article are the ones you have most likely already dealt with. Therefore, we have chosen them with the intention of helping you recognize them more easily and advising you on how to better protect yourself from them.
Phishing, Smishing, and Vishing
Phishing attacks consist of messages, usually emails, posing as trusted or reputable entities, sent by malicious actors with the intent to deceive a person into revealing (sensitive) information, installing unwanted software, or granting unauthorized access. Other forms of phishing include smishing, which occurs via SMS, and vishing, which occurs via phone calls.
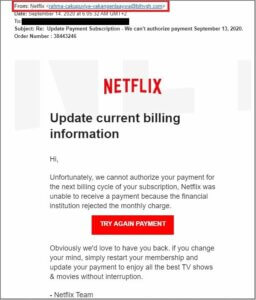
How to defend against it as a user:
- Be mindful to whom you give your email address or phone number;
- If you were not expecting that email or SMS, or if you don’t recognize the sender, just delete the email or SMS;
- If you opened the email or SMS, because you were unsure of the content’s relevance, don’t save any files that may be sent as attachments without ensuring that they are safe;
- Additionally, if there are any links present in the email or SMS, don’t click it the second you see it, first, verify with attention if the link redirects to a reliable source, and then you can consider clicking it;
- If a seemingly reputable company asks for sensitive information on a phone call you were not expecting, say you can not attend now and call them yourself immediately after.
How to defend against it as a company:
- Ensure that your employees receive proper training on a regular basis;
- Establish and maintain bring-your-own-device policies;
- Configure email spam filters and install anti-phishing software;
- Enforce password policies and use multi-factor authentication.
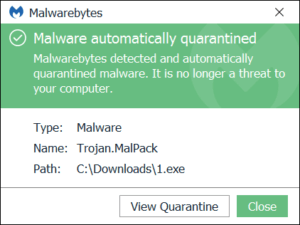
Malware
Malicious software that is fraudulently installed on a machine with the specific intent to disrupt or damage it. The most common types of malware are viruses, worms and Trojans.
How to defend against it as a user:
- Backup your files regularly;
- Always check the sources of the files/executables you download from;
- Always pay attention to what programs are installed on your computer and install only what you really need;
- Try to keep the installed software up-to-date;
- Install software on your system such as antivirus and malware scanners that are capable of detecting and deleting malware. This software must be certified and developed and retrieved from well-known and trusted companies.
How to defend against it as a company:
- Backup your data and make sure recovery procedures are working properly;
- Configure your firewalls, and implement IDS (Intrusion Detection System) and IPS (Intrusion Prevention System);
- Create and enforce security policies and, continuously, update them when needed;
- Partition your network using network segmentation.
Social Engineering / Hacking
Malicious actors exploit a victim’s psychology to perform unintended actions. A common social engineering attack is manipulating the trust someone has in someone or something, i.e., the malicious actor impersonates someone using information commonly available in social media networks, personal conversations, data leaks, etc., and asks the victim to do something that will benefit the malicious actor and harm the victim.
How to defend against it as a user:
- If something seems too good to be true, it probably is. Always be skeptical of great offers, they are most likely a scam;
- Always be suspicious when a behavioral change happens to someone;
- Do not share your personal data or passwords with others over the Internet. If you really have to, change them as soon as the other person no longer needs them;
- Be mindful of what you post online, where you post it and who has access to it;
- As with phishing, a form of social engineering, do not click on links or download files before checking the source and purpose of the file.
How to defend against it as a company:
- Implement and enforce a zero-trust model;
- Be mindful of what information is posted on the company’s social media, and what is thrown into the trash, whether it is physical or virtual;
- Organize drills that simulate social
Conclusion
After all these explanations, there is one main takeaway that we would like you to retain, which you have probably already done, if only implicitly: YOU and your behavior are the best defense mechanisms against cyberattacks.
However, it is clear that these mechanisms alone do not work by themselves, and must be complemented by tools and frameworks that make the job easier and allow for more detailed and faster assessment. This is why the use of artificial intelligence, machine learning, and automation—tons of automation—is increasing by leaps and bounds, enabling the vast amounts of data being generated and attacks being carried out to be processed in a matter of seconds. This allows people to closely monitor the more sophisticated and severe attacks, learn from them, and use the insights to improve the tools and methods used, as the field of cybersecurity, like many others in tech, is constantly updating and evolving.
If you need trained and highly professional people to help you achieve the highest level of security in your organization, contact us, and we will connect you with the most talented cybersecurity experts.